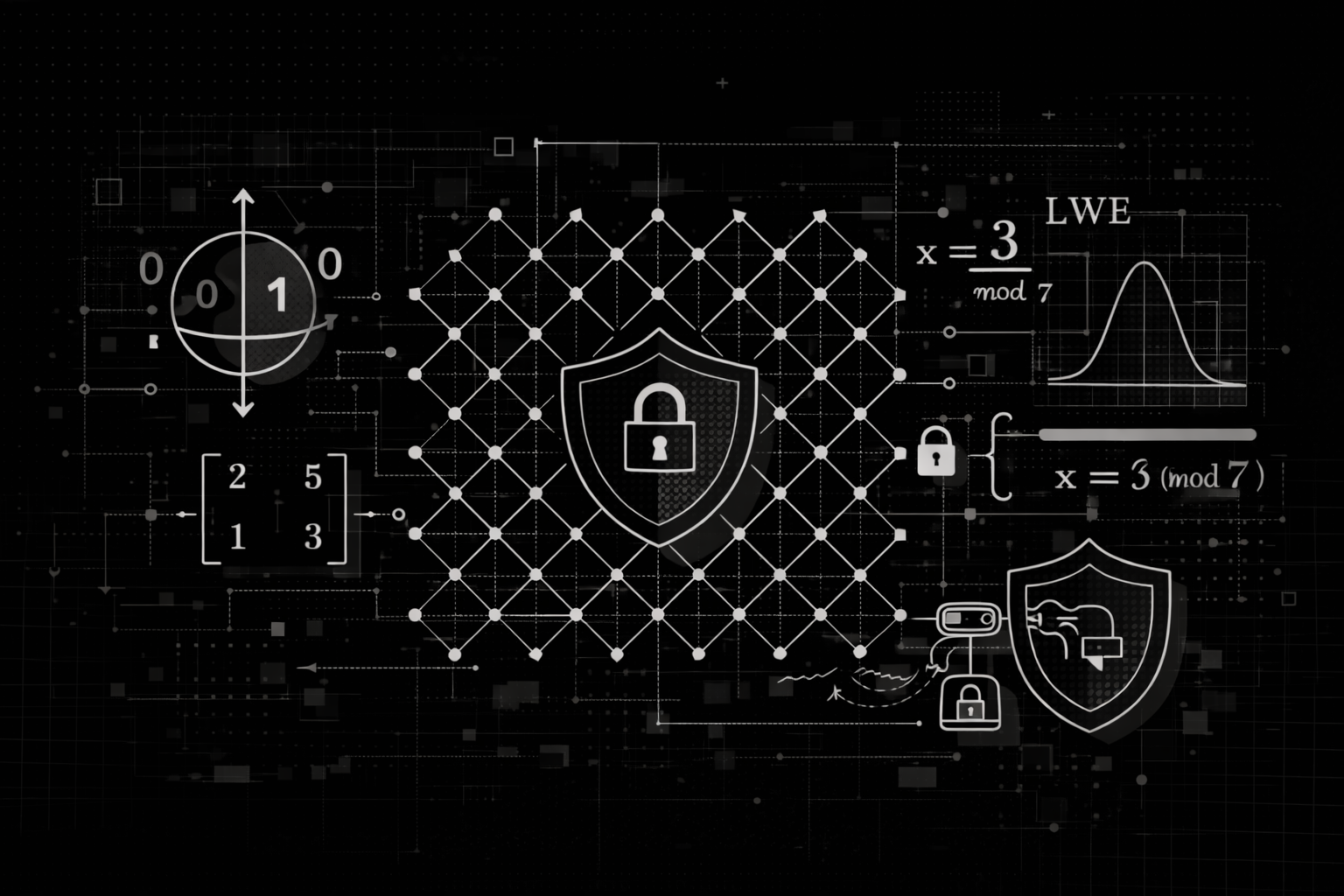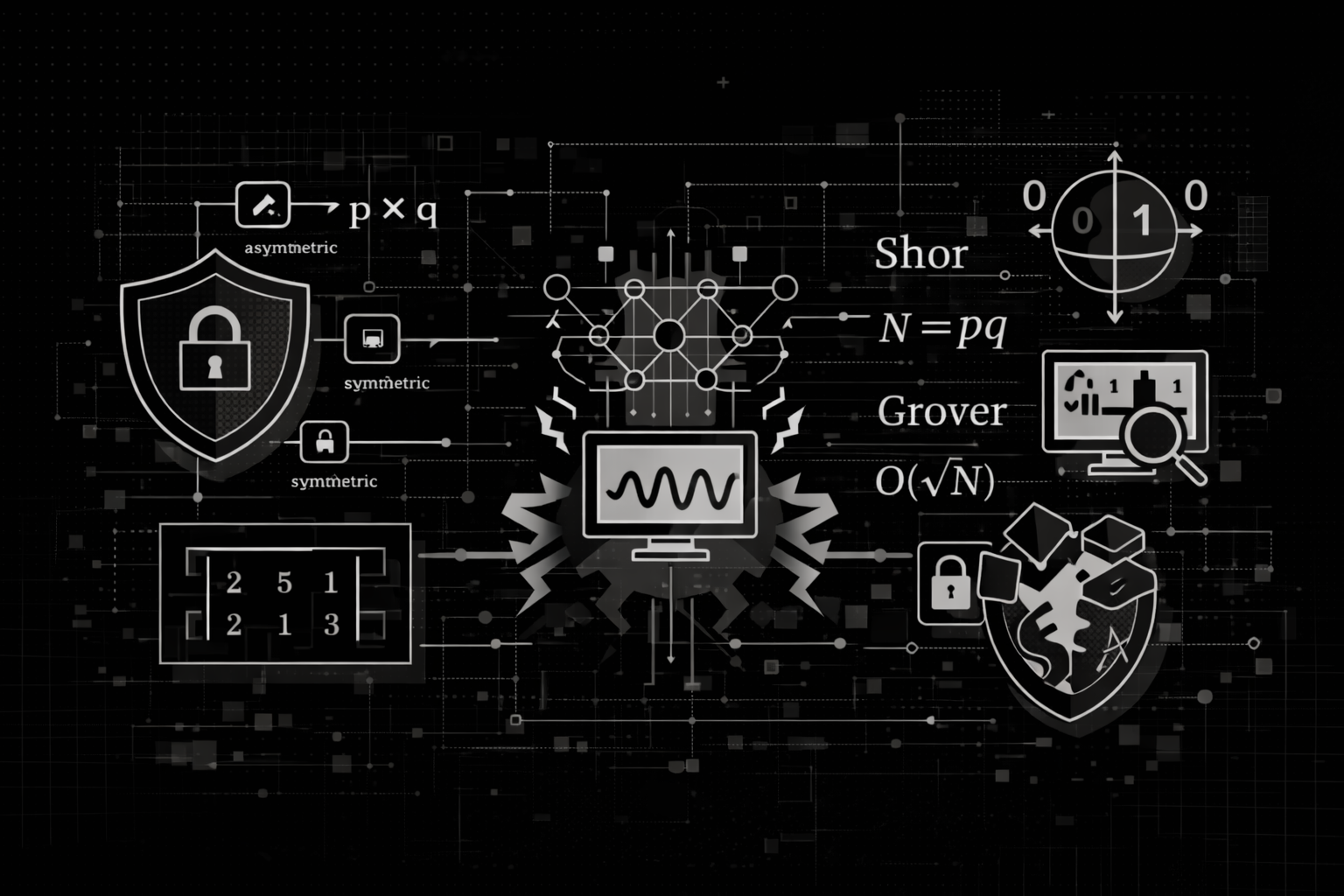
Post-Quantum Cryptography: Alternative Mathematical Frameworks and Cryptanalytic Lessons
A comprehensive exploration of non-lattice post-quantum cryptography: hash-based signatures (SLH-DSA), code-based encryption (Classic McEliece), isogeny-based cryptography (and the SIKE break), and multivariate schemes.